Current security events have again shed light on hybrid Russian activities in Montenegro, this time through a well-organized intelligence network, with the aim to collect confidential data of a NATO member. The epilogue of the activities carried out on September 29 by partner intelligence agencies and competent Montenegrin authorities, primarily the Ministry of Interior and the National Security Agency, was the denial of residence for 6 Russian diplomats and the ban on entry to Montenegro for 28 foreign citizens who, as stated, worked for the interests of foreign services. A former spokesman for the Ministry of Foreign Affairs, Radomir Sekulović, is among those suspected of working for the Russian intelligence service.
According to publicly available sources, the National Security Agency (ANB) owns information that Sekulović was part of a spy network formed by an intelligence officer of the Russian Military Intelligence Service GRU, Igor Zaytsev.
The ANB recorded the arrival of Zaytsev in Montenegro on several occasions, the last time in 2018 when he had contact with Sekulović. It was then revealed that the Russian intelligence officer had brought new equipment for encrypted communication, which he handed over to Sekulovic, which is precisely the modus operandi of the intelligence network that Zaytsev formed and led across Europe.
Sekulović held that position in the MFA during the time of the Serbia and Montenegro state union, was employed in consular affairs for over 30 years and had a high rank even in the former Yugoslavia. It is indicative that Sekulović worked for a long time in consular affairs in African countries at a time when Igor Zaytsev, as a member of the Fourth Department of the GRU, was in charge of Africa.
Who is Zaytsev?
Igor Zaytsev, born on April 6, 1954, led the GRU intelligence network that operated in several European countries and included members of the administrations of those countries since the 1990s.
After a tip-off to the Austrian authorities, in 2018, one of the most successful operations led by Zaytsev was discovered, i.e., his connections with the Colonel of the Austrian Army, Martin Möller, who was found guilty by the court and sentenced to three years in prison in 2020 for giving confidential military information data to Russia. Meanwhile, an Austrian court has issued an arrest warrant for Zaytsev after uncovered evidence suggested he was the main point of contact for the Austrian Colonel.

According to available data and evidence, Zaytsev trained Colonel Möller to use the sophisticated communications equipment he used to transmit classified information to Moscow. Möller was thoroughly trained to connect with Russia’s Strela-3 military satellites as they flew over Central Europe.
The retired Austrian Colonel cooperated with the Russian military intelligence service since 1987, receiving at least 280,000 euros in return. He spent the last five years before his retirement working in the Structural Planning Department of the Austrian Ministry of Defense in Vienna. Martin Möller gave Russia classified information on aviation, artillery and the migrant crisis.
As a colonel of the partner army, he participated in several NATO events, so he got detailed information about the methods the Alliance uses to protect against attacks by improvised explosive devices –one of the most frequently used weapons by the Taliban against allied troops in Afghanistan.
He was an important asset of the GRU because of his frequent encounters with Russian spies not only in Austria but also in Slovakia, the Czech Republic, Croatia, Hungary and Slovenia. He was specially trained and had at his disposal the technique for successfully carrying out espionage activities for the needs of Russia. During his espionage career, Möller personally met with Russian agents, some of whom are also known for their activities in Montenegro. One of them is Eduard Shishmakov, who was sentenced by the High Court in Podgorica to 15 years in prison for participating in an attempted terrorist attack on the day of the parliamentary elections in Montenegro in 2016.
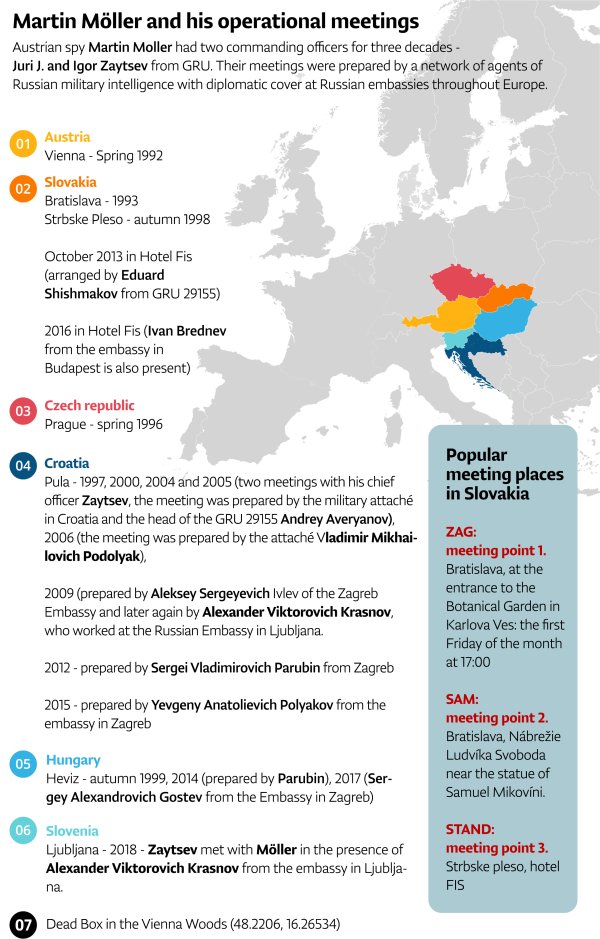
In addition to Shishmakov, Möller also met with the commander of his unit 29155, Andrei Averyanov. This unit is specialized in assassinations or sabotage to destabilize European countries. Among other things, it was behind the poisoning of Sergei Skripal and his daughter in Salisbury, England, the planting of an explosion in an ammunition warehouse in the south of the Czech Republic in 2014, when two Czech soldiers were killed, as well as the attempted coup in Montenegro in 2016.


Igor Zaytsev supervised not only Möller but also the entire intelligence network of GRU agents operating under diplomatic protection in the Central European region – who communicated with him or were sent to collect information.
These were the same agents Slovakia expelled in 2020 after the misuse of Slovak visas in the assassination of a Chechen activist in Berlin. godine nakon zloupotrebe slovačkih viza u atentatu na čečenskog aktivistu u Berlinu.
GRU activities in cyberspace
In the period of the finalization of Montenegro’s accession to NATO, which coincided with the parliamentary elections in October 2016, Russia significantly activated and intensified its presence not only through disinformation campaigns by the Russian media and coup attempts but also through cyber-attacks by the GRU, i.e., their ATP28 group Advanced Persistent Threat 28, known as Fancy Bear.
According to our data, the most severe cyber-attacks by the GRU (not taking into account the cyber-attacks on government infrastructure from August 2022, where the epilogue of the investigation is still awaited) in Montenegro took place in 2017 at the time of Montenegro’s accession to the NATO alliance and on the day of the parliamentary elections in 2016.

During three months of 2017, the services of the Government and state institutions and some pro-government media were threatened. The Montenegrin Ministry of Defense then reported that it was the target of a ‘phishing attack’ through emails that appeared to come from the EU and NATO with attachments, and which allowed hackers to install the Gamefish malware on Ministry of Defense computers, which are the exact methods used by the APT28 group.
A Gamefish is a Trojan (virus) that offers a hacker extensive access to a targeted computer, including data exfiltration, log access, and other surveillance capabilities. US intelligence has further indicated that the APT28 group is linked to the Russian military intelligence service GRU and funded by the Kremlin. APT28 was also found to be responsible for attacks on the German Bundestag in 2015, French television station TV5 Monde, an attempted attack on the Organization for the Prohibition of Chemical Weapons (OPCW), and the 2018 Pyongyang Winter Olympics.
On the day of the parliamentary elections on October 16, 2016, Montenegro faced frequent DDoS attacks (distributed denial of service attacks), which targeted websites of state institutions, pro-NATO and pro-EU political parties, civil society websites, and election observers. As a result of these activities, the information and websites of some political parties were hacked.
After a series of attacks, at the beginning of 2017, Montenegro requested the help of NATO and Great Britain, which helped to successfully repel two attacks at the end of the same year.
Due to these events, at the beginning of October 2019, members of the US Cyber Command arrived in Podgorica to investigate signs of Russian penetration into the networks of the Montenegrin government but also to create an insight into opposing cyber threats in anticipation of the then-upcoming US and Montenegrin elections in 2020.
Based on information in the Montenegrin media, as well as publicly available data on previously identified cases of Russian agents operating in certain European countries, including Montenegro, it is evident that the Russian Military Intelligence Service (GRU) has developed its agency network in Europe, which primarily aimed at collecting data on the activities and structure of NATO and the destabilization of individual member states of the Alliance, which DFC has written about before. It is evident that specific Russian agents, who also carried out their activities in Montenegro, are members of the same network that has been coordinated from the same center of activity for years. In this regard, the case of the Austrian Colonel Möller is indicative, based on which it is possible to establish an analogy with the methodology of the Russian agency network in the region as well, bearing in mind the current security events and opportunities.

